About me
Harnessing a commitment to relentless self-learning, I possess expertise in both offensive and defensive cybersecurity operations. My curiosity fuels a creative approach to defending digital environments, where I translate complex concepts into actionable insights to enhance organizational security. Passionate about empowering teams and fostering a culture of security awareness, I strive to contribute to a safer digital landscape.
Beyond cybersecurity, I am a multifaceted individual with a thirst for knowledge. My interests include chess, music, reading diverse books, philosophy, and meditation. As an INTJ-T personality type, I thrive on deep thinking and introspection, constantly seeking to expand my understanding of the world.
02+
Years of
Experience
03+
Years of Self Learning Experience
08+
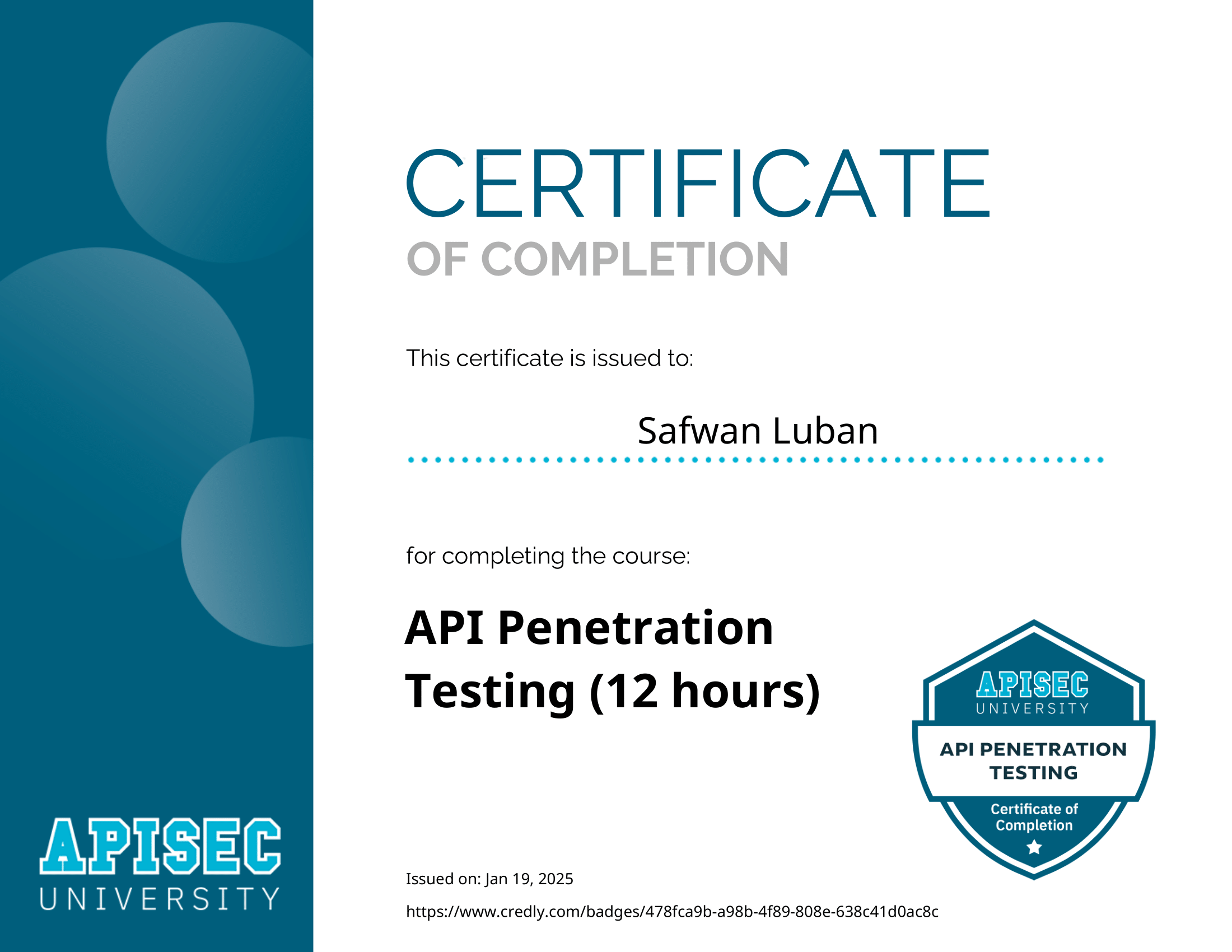
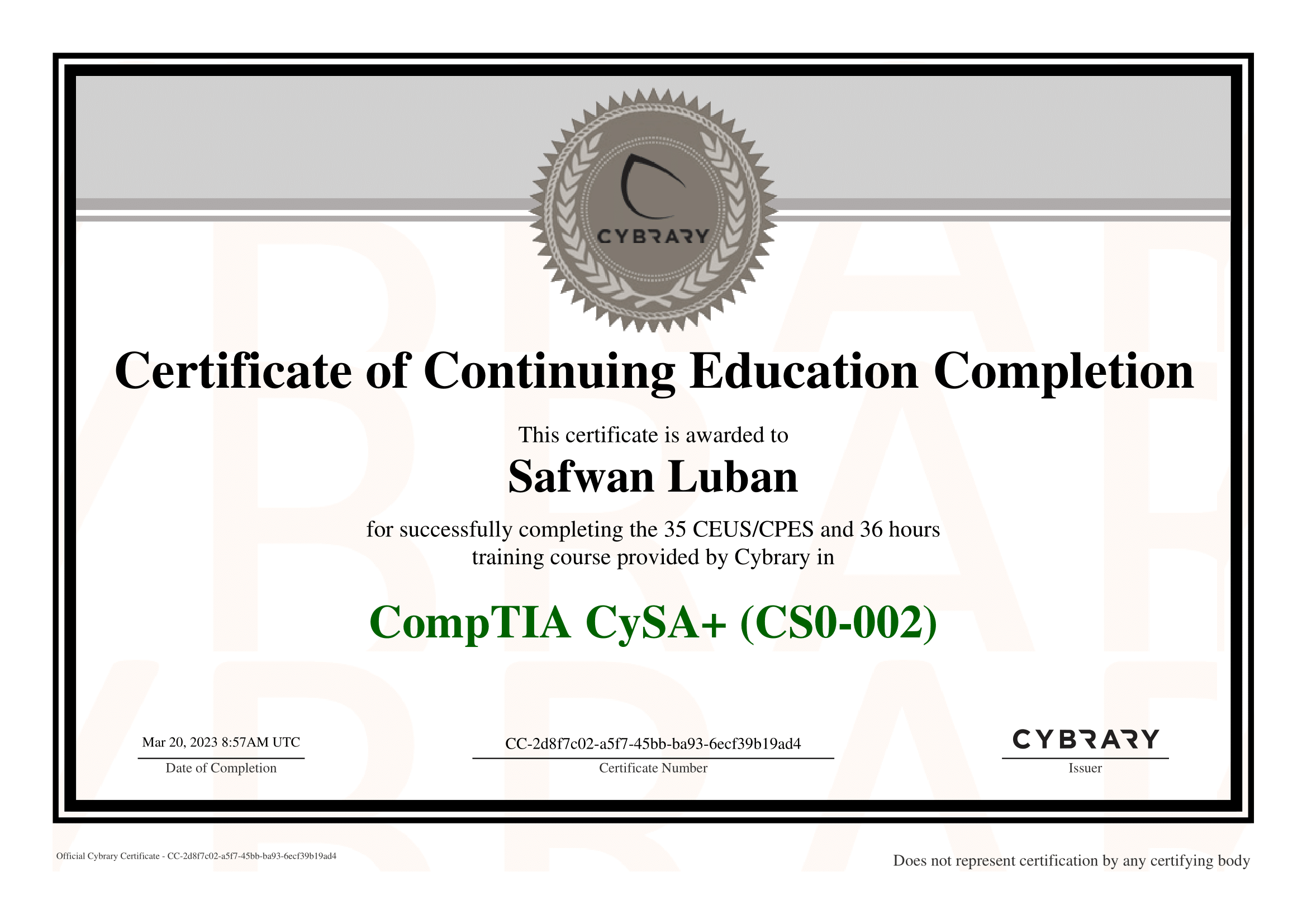
Certifications
Earned
24+
CTF's
Participated
Portfolio
-
GitHub
Projects -
Medium
Articles -
LinkedIn
Safwan Luban -
Credly
Badges -
Hack The Box
Pro Hacker -
TryHackMe
Top 3%
What I'm Doing
-
Freelance Security Researcher
Providing various security services including Article Writing, Vulnerable Lab Making, Training, Pentesting, and Vulnerability Assessments on a freelance basis.
-
Security Content Creation
I conduct research on various security vulnerabilities and exploits, and I create blogs and vulnerable machines based on my findings to help new security professionals learn about different techniques.
-
Self Learning
Continuously learning and practicing both offensive and defensive techniques to grow as a hacker. Practicing both offensive and defensive techniques is going to give me both attacker's and defender's perspective.
-
Chess
I am committed to mastering chess, as it is a game that has been shown to improve a wide range of soft skills, such as stress management, critical thinking, and problem-solving.